This is part 2 in my series of blog posts covering HP Connect for Intune. The first post covered how to get the BIOS patched to the latest release. Today I cover the BIOS authentication, which is an important aspect of managing, controlling and securing Windows devices. If the BIOS can be accessed without authentication, a local or remote user may be able to disable basic security features, perhaps introducing malware early into the startup process that Windows may not protect against.
The ultimate goal is to have a security boundary covering all aspects from chip to cloud. An UEFI BIOS is the chip containing the hardware start-up code and many settings that should be secured prior to booting into a Windows Operation System. We will manage the BIOS security limiting setting changes only to users or administrators with knowledge of the authentication mechanism.
Please note: This is not a sponsored post!
In part1 of my series of blog posts covering the HP Bios security I covered how to make sure the HP Bios was updated with the latest version through Intune. You can find this post here: Simon does...: HP Connect for Intune, Part1: BIOS Update (skotheimsvik.blogspot.com)
HP Connect supports two types of BIOS authentication policies:
- HP Sure Admin
- Passwords
While BIOS passwords can help secure access, they have some drawbacks like all passwords have as a protection mechanism.
- Having a common BIOS password set across all devices in the organization opens for leakage and accessible outside of the secure environment eligible to have access
- Passwords tend to change over time. This may leave some devices with inconsistent BIOS password, and it will be hard to keep track of what device have which password set.
- Passwords are used in clear text on the devices and may thus pose a security threat.
In part2 I will cover the secure passwordless version of accessing the HP Bios by use of HP Sure Admin. Both remote and local F10 setup access can be configured using BIOS authentication policies to require the use of the HP Sure Admin app to authenticate the user/administrator.
HP Sure Admin
HP has developed a PKI tool to secure access to the BIOS, both remotely and through local F10 management. This is tightly connected with the HP Secure Platform Management (SPM) which is the trusted base found in the UEFI Bios of each device.
OpenSSL and Certificates
The SPM solution utilizes a pair of cryptographic keys as base for the security - the endorsement key and the signing key. These certificates need to be created and securely stored by the company as these are not managed or stored in the HP cloud. HP only retrieves the embedded public/private key pairs from the certificates which is kept in a secure cloud vault and used when creating a HP Sure Admin authentication policy. An additional certificate is used to support the F10 setup protection.
I will use OpenSSL to create my required certificates. There is a good description for the process of installing OpenSSL here: How To Install OpenSSL on Windows – TecAdmin. I often tend to do such stuff in Windows Sandbox as described in my previous blog post on creating a LAB environment: Simon does...: Building a MEMpowered LAB environment (skotheimsvik.blogspot.com)
After installation of OpenSSL in the Sandbox environment, I set some system variables:
Create Endorsement Key Certificate
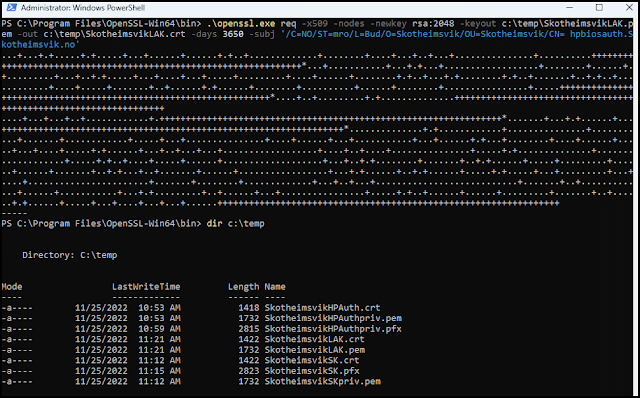
With the OpenSSL environment established, I am ready to create the x.509 self-signed endorsement key certificate. This is done by the following code.
.\openssl.exe req -x509 -nodes -newkey rsa:2048 -keyout C:\temp\SkotheimsvikHPAuthpriv.pem -out c:\temp\SkotheimsvikHPAuth.crt -days 3650 -subj ‘/C=NO/ST=mro/L=Bud/O=Skotheimsvik/OU=Skotheimsvik/CN=hpbiosauth.skotheimsvik.no’
.\openssl.exe pkcs12 -inkey C:\temp\SkotheimsvikHPAuthpriv.pem -in C:\temp\SkotheimsvikHPAuth.crt -export -keypbe PBE-SHA1-3DES -certpbe PBE-SHA1-3DES -out C:\temp\SkotheimsvikHPAuthpriv.pfx -name ‘Skotheimsvik SPM Endorsement Key Certificate’
After providing a password for the certificate, the PFX file is ready in the folder.
Create Signing Key Certificate
At the same way as with the endorsement key certificate, I will create a X.509 self-signed signing key certificate.
.\openssl.exe req -x509 -nodes -newkey rsa:2048 -keyout c:\temp\SkotheimsvikSKpriv.pem -out c:\temp\SkotheimsvikSK.crt -days 3650 -subj ‘/C=NO/ST=mro/L=Bud/O=Skotheimsvik/OU=Skotheimsvik/CN= hpbiosauth.skotheimsvik.no’
.\openssl.exe pkcs12 -inkey c:\temp\SkotheimsvikSKpriv.pem -in c:\temp\SkotheimsvikSK.crt -export -keypbe PBE-SHA1-3DES -certpbe PBE-SHA1-3DES -out C:\temp\SkotheimsvikSK.pfx -name ‘Skotheimsvik SPM Signing Key Certificate’
Create Local Access Key Certificate
Finally, I use the same routine to create a X.509 self-signed Local Access Key (LAK) certificate.
.\openssl.exe req -x509 -nodes -newkey rsa:2048 -keyout c:\temp\SkotheimsvikLAK.pem -out c:\temp\SkotheimsvikLAK.crt -days 3650 -subj ‘/C=NO/ST=mro/L=Bud/O=Skotheimsvik/OU=Skotheimsvik/CN= hpbiosauth.Skotheimsvik.no’
.\openssl.exe pkcs12 -inkey c:\temp\SkotheimsvikLAK.pem -in c:\temp\SkotheimsvikLAK.crt -export -keypbe PBE-SHA1-3DES -certpbe PBE-SHA1-3DES -out C:\temp\SkotheimsvikLAK.pfx -name ‘Skotheimsvik SPM Local Access Key Certificate’
The PEM and CRT files could safely be deleted. The PFX files and the corresponding passwords should be saved safely.
HP Connect Policy
We are now ready to create the authentication policy in HP Connect.
- Sign in to https://admin.hp.com as a Global Admin for the tenant
- Navigate to Policies in the left pane and create the new policy
- Select Sure Admin and click on "New SPM" and "New LAK" to upload the previously created self-signed certificates.
- The new SPM and LAK configurations can now be selected and the policy can be saved.
- The policy can now be assigned to a group.
- Pick a group suitable for the purpose. This should initially be a group with a limited set of devices to pilot the configuration before it hits globally in your environment.
- This policy will now be added as a proactive remediation policy in Intune. Please note, there will be one proactive remediation policy pr. assigned group.
HP Sure Admin App Access
Grant access
To give access for non-administrative accounts to access the F10 setup on the endpoints, access can be granted in Azure Admin center. This is where we can allow field support personnel to obtain secure in-person access to BIOS setup. Think carefully about the following setup to make it fit in with the rest of your RBAC setup.
- Start portal.azure.com and navigate to Enterprise Applications.
- Locate the "HP Connect for MEM" application and open this.
- Select "Users and Groups" found in the Manage column on the left.
- Add the AAD group containing the users allowed to sign in on the BIOS through the HP Sure Admin app. Note: When you assign a group to an application, only users directly in the group will have access. The assignment does not cascade to nested groups.
Use the app for authentication
The app can easily be downloaded and installed from GooglePlay/Appstore.
When the technician is physically at the endpoint, they can press F10 while booting the device to access the BIOS.
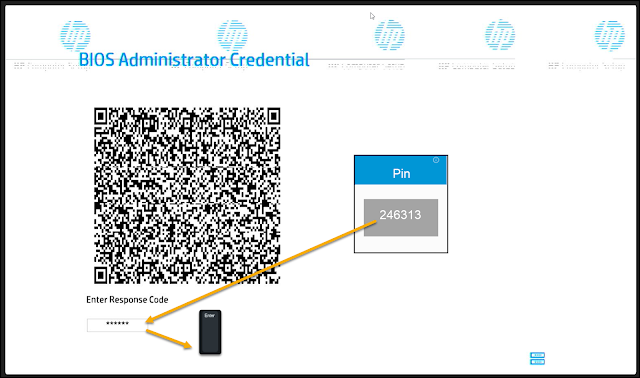
When Sure Admin is enabled, the device will present a QR code to be scanned by the HP Sure Admin app on the cell phone.
The code should be entered below the QR code followed by Enter.
Removing BIOS authentication Policy
The settings in the BIOS are now protected for unauthorized access. With decades of experience performing computer management, I have no problems finding reasons why this type of policy needs to be discontinued from some devices. If I add fantasy, even more reasons pop up.
If we remove a BIOS authentication policy from a device group, a "no-authentication" policy will be published to the same group.
This change will undo previous authentication policies of the devices in the selected group. The BIOS on these devices will be wide open for access with no password protection. Please be aware that this can take some time since the device needs to check-in to Intune to get the deprovisioning policy.
The Requirements
I guess this has piqued your curiosity and you are now wondering what is required to set this up.
HP Sure Admin is a capability included in select HP PCs at no additional cost, just like the HP Client Management Tools required to configure and manage Sure Admin. HP Sure ADmin is supported on a wide range of HP business products including Pro, Elite and Z desktops/notebooks.
The solution is based on Proactive Remediations which requires devices to be azure AD joined, managed by intune, running enterprise/pro/edu editions of Windows 10/11, enrolled into endpoint analytics. The device also requires Enterprise E3/A3/E5/A5 license.
Next step: Bios Settings
Ideally, we should not have to log into the BIOS to make manual changes. In my next blog post on this topic, I will explore the HP Connect BIOS setting policy and how we can use this tool to set the desired BIOS settings centrally.



























No comments:
Post a Comment