Imagine a compromised administrative account going wild in your Intune environment. Wouldn't it be great to protect your configuration with a second factor, like MFA? Join me while I experience the new Multiple Administrative Approvals (MAA) feature for Intune which is out in public preview!
By using Intune access polices we can require a second administrative account to approve changes in the environment before they are applied to the production environment. This can give associations to MFA (Multi Factor Authentication), but let's welcome MAA (Multiple Administrative Approvals) instead.
The goal for MAA is to protect specific configurations. At the time of writing the feature of MAA is in public preview and the available options is to protect Apps and Scripts for devices. I do hope this will be extended to other parts of Intune as well. It seems natural to add this security layer also to Security Policies, Device Configuration Policies, App Configuration Policies, App Protection Profiles and so on.
The introduction of MAA will have an impact on the change process around Intune since changes now needs to be validated before they are effectively implemented.
Defining approvers
The approval can only be performed by another user account than the one creating the change. This introduces two MAA roles:
- The change requester which must be assigned the Intune Services Administrator or Azure Global Administrator role.
- The approver which must be in an approval group assigned to the access policy. The user must also have the same privileged roles as the change requestor. It is not enough to just be a member of the approval group.
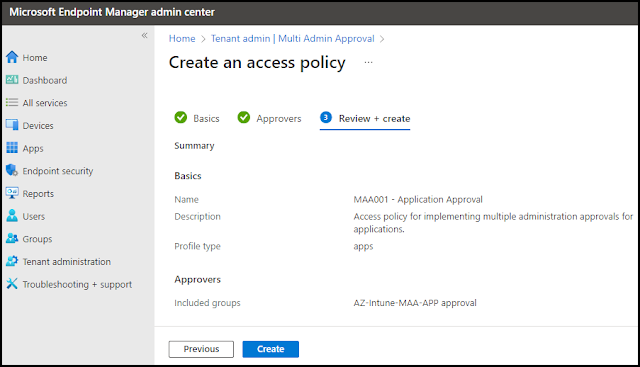
Define Intune Access Policies
I will now select the profile type of Apps to limit any action on an application in Intune. This will include actions like create, edit, assign and delete on applications.
Verify the MAA experience
Add a new application
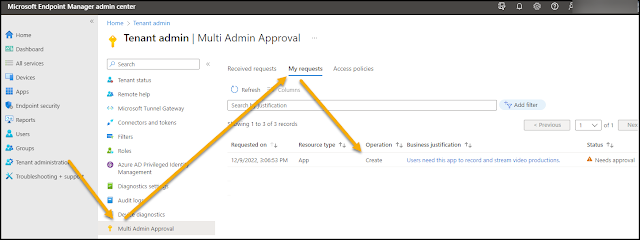
After saving the application, I can find my requests in a list at Tenant administration - Multi Admin Approval - My requests:
I would have wished for an updated status in the application list above, but I have to click the application to get this kind of detailed information today.
Delete or change and application
As mentioned, I am not allowed to approve my own requests. I have to ask a colleague with the correct RBAC role, and which is a member of the app approval group to handle this. Please note that there is no automatic notifications in the solution today.
The list will be updated with the new status, and the approver note will be visible when checking the details of the request.
Verify the application
Once approved by the approver, the change requestor will be notified in his own portal if he stays signed in.
Concluding the experience
The importance of this function is nevertheless highly relevant with its extra layer of security applied to the change process around Intune.






















No comments:
Post a Comment