Mobile devices can be a challenging asset to manage and keep secure with their many variations in ownership, management and operating systems. This blog post will give you some ideas on how you can enforce a minimum version of the operating system on the mobile phones accessing the company's data in Microsoft 365.
The cell phone is for many users the edge of privacy where they can accept the company's administration. At the same time, it is important for the company to have control over its data and applications.
An important prerequisite must be set from the orgranization - Yes, users can have access to data, under defined conditions. One important security measure is to ensure updated software regardless of management mode. Let us dive into the condition of having updated operative systems on the mobile device accessing company data.
MDM and MAM in Microsoft Intune
I will not do a wide coverage of MDM, MAM and Intune in this post, but these are components we use to ensure devices accessing the company's data are having a desired state of health.
While Mobile Device Management (MDM) is a way of securing devices such as smartphones and tablets, Mobile Applications Management (MAM) secures the applications on smartphones and tablets accessing the organizational data, such as the Outlook, Office and Teams apps. Microsoft Intune is the cloud-based service found in Microsoft 365 utilizing MDM and MAM to secure the company's digital interests when data is consumed on mobile devices. Intune can enforce policies to devices and applications to ensure the data is kept within organizational boundaries.
Vulnerability Management
It is recognized that operating systems over time get known security flaws. The best solution for this is patching. Always ensure that the latest available version is installed.
Microsoft 365 Defender offers vulnerability recommendations, and some of these will deal with operating system versions on mobile devices found through MDM and MAM. This is information we can take into consideration when we offer access to the company's data.
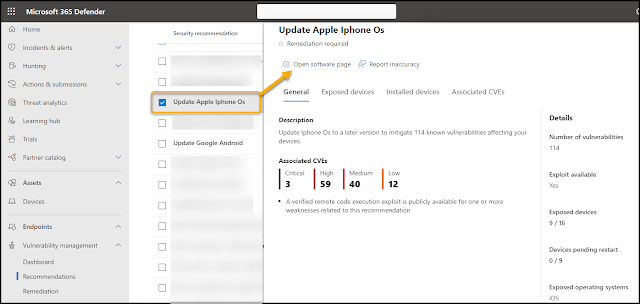 |
| Example of recommendation from vulnerability management addressing Apple iOS version |
Inside Microsoft 365 Defender Portal we find recommendations for upgrading the operating system versions for Apple and Android devices. This information will include details of which devices are exposed, which versions of the operating system are involved as well as how many weaknesses each version has.
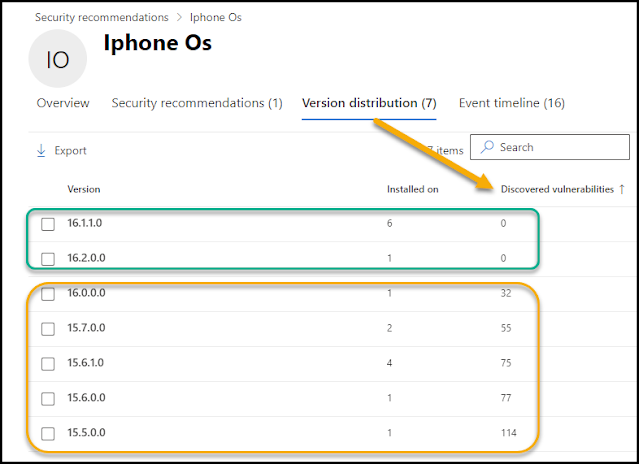
By clicking the link named "Open software page" we can find detailed information of version distribution and number of vulnerabilities pr. version. These are numbers we could base our assessment on which versions of the operating system we allow.
Generally, most iPhone devices will receive system and security updates for five to seven years after release. Android devices have a much shorter period, only receiving these updates for 2-3 years after the release of a device. This should be an important variable when assessing the company's mobile devices since some devices potentially have a longer lifespan.
Enforcement of OS through MAM
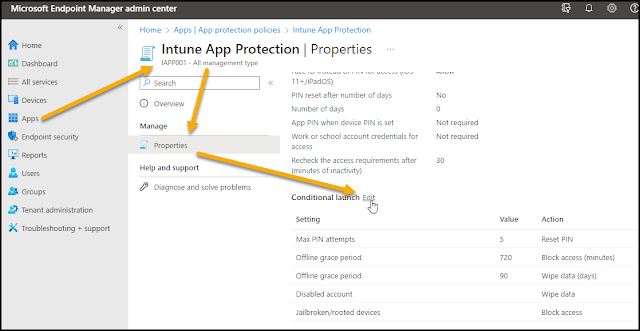
MAM is using App Protection policies to enforce the desired level of security in the applications. Inside these policies we can set conditional settings related to the operating system version.
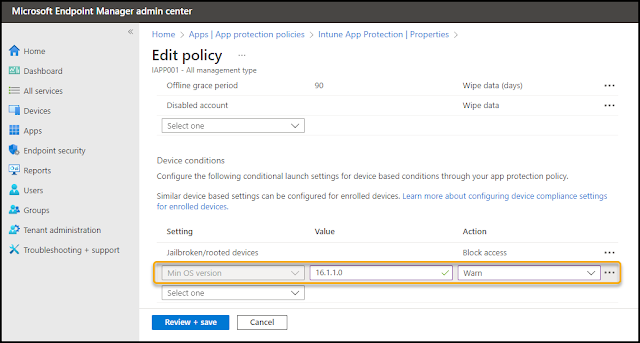
The example below shows a setting that will give a warning to the end user if their iOS device has an OS version lower than 16.1.1. This warning will inform the user to update the OS to the latest release, but it will not deny access to the application and data. This should stimulate an update of the operating system on the device.
If you find that one specific version of the operating system has to many vulnerabilities, you can even block access instead of just give a warning message to the end user.
This will force the user to update the operating system on their device before they are allowed to access the corporate application and data. This can be a reasonable sanction for Apple devices that have the option to update. For security reasons, this kind of sanctions should be implemented also for Android devices - but be aware that this can potentially force recirculation of devices since the lifespan of available updates are poorer for Android devices.
Enforcement of OS through MDM
MDM is using Compliance policies to control the desired level of security for the enrolled devices. The compliance state of the device will be an important signal for Conditional Access rules, which in turn can block users and devices that don't meet the compliance rules.
The device compliance policy can be configured as platform-specific rules defining requirements for devices to be considered compliant. This includes settings for device encryption, device health, minimum operating system version and more.
This is where we define the minimum version of operating system we allow for a device to be marked as compliant.
The sanction from this setting is defined by Conditional Access policies and how you have set up access for devices that do not meet compliance. Should they be blocked? Should they provide MFA each time, or other outcome?
Compliance notifications
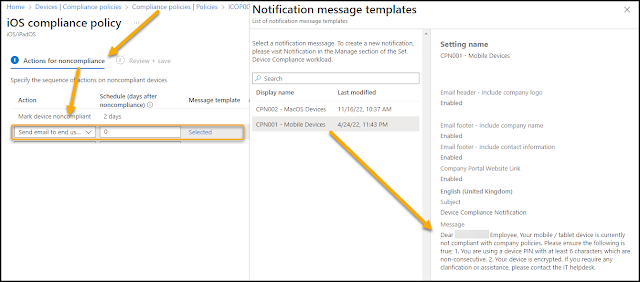
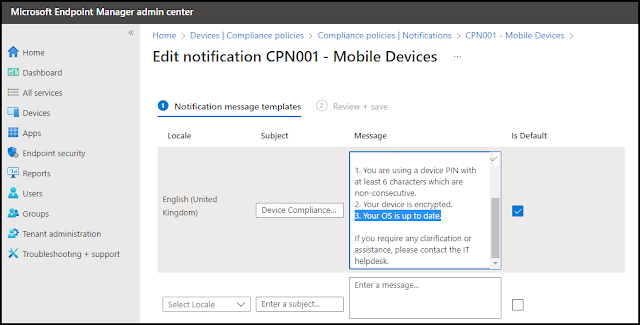
You should now create a compliance notification in Intune for notifying users who are out of compliance and inform them of what they need to do next to (re-)gain access to corporate data. This could be information sent by e-mail with the actual company branding and tailored information for the current configuration.
The message templates can be configured in Intune admin center - Devices - Compliance policies - Notifications.
Let Intune stimulate mobile updates
By setting this configuration, it should be possible to use Intune to stimulate your users to keep their mobile devices up to date. This will in turn reduce the attack surface for your users' devices, both for privately and professionally use case.
Security happens one step at a time - let's take this step together today!





No comments:
Post a Comment